Windows Server 2012 introduces a plethora of new features with a key emphasis on Cloud integration being the buzz word in the industry over the last 24 months. Windows continues to grow and mature as an operating system with the latest iteration being more secure, reliable and robust and more importantly making it easily interoperable with other systems.
This post will focus on Installing a Windows 2012 Server and then promoting it as the first domain controller in a new Forest. Even though the logical steps haven’t really changed dramatically since the introduction of Windows 2008, the interface has! especially with the new metro look. So let’s begin our journey with Windows Server 2012 as this will be the first of many articles on configuring different components that Windows Server 2012 has to offer.
Installing Windows Server 2012
The first step is to boot up from the CD or ISO image and select your language settings.
The installation will eventually re-start your Windows Server where it will go through the final stages of preparing the environment for first time use.
You will eventually be prompted to enter a password for the built-in Administrator account.
Click Finish
Hit Ctrl – ALT – Delete to sign in, and enter your password.
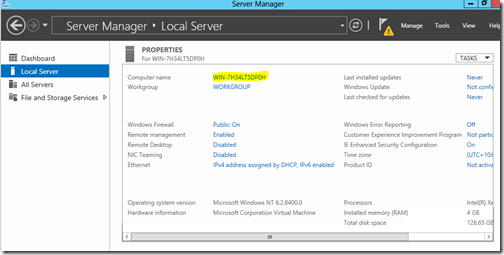
First thing I want to do is change the computer name. Windows goes ahead and provides a default unique name in the form of WIN-<random characters>
This will take you to the all familiar System Properties
Click Change, enter a more desirable Computer Name and then click OK.
Click Next
Click Next
Click on Add Features
Click next
Upon completion you will be presented with an installation succeeded message.
Click Close.
You will now be presented with the All Servers Task Details, in which you will click on Promote this server to a domain controller under Action.
Click Next
Click Install
Let’s begin by creating our first Organizational Unit that will house our corporate users (I am not a fan of using the default Users). On the right navigation pane under Taks > <domain name> click on New and then select “Organizational Unit”.
This post will focus on Installing a Windows 2012 Server and then promoting it as the first domain controller in a new Forest. Even though the logical steps haven’t really changed dramatically since the introduction of Windows 2008, the interface has! especially with the new metro look. So let’s begin our journey with Windows Server 2012 as this will be the first of many articles on configuring different components that Windows Server 2012 has to offer.
Installing Windows Server 2012
The first step is to boot up from the CD or ISO image and select your language settings.
Select your Language and input options and then click on Next.
Click Install Now
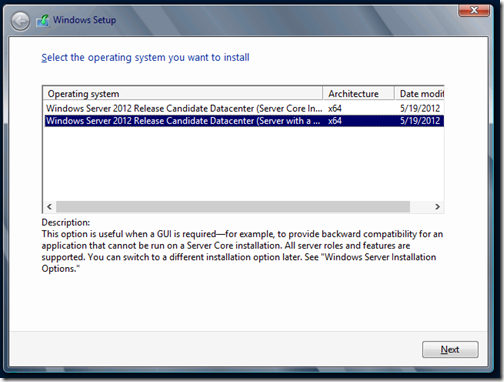
Select the operating system you want to install. I have selected Windows Server 2012 Release Candidate Server with a GUI. The other option is server core which was first introduced in Windows 2008 and is a minimal install with no GUI but provides remote management through Windows PowerShell and other tools.
Click Next
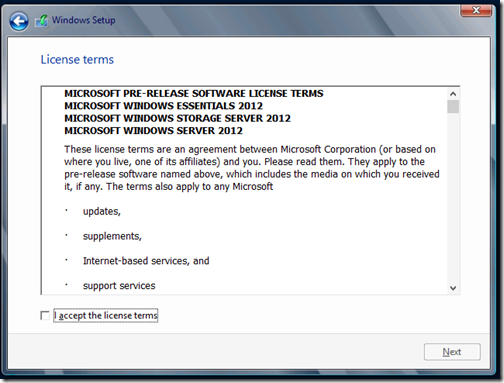
Accept the License terms
Click Next
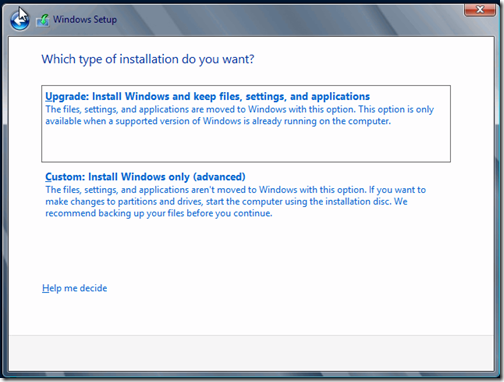
We are performing a new installation of Windows Server, so click on Custom.
The Installation of Windows then proceeds.
The installation will eventually re-start your Windows Server where it will go through the final stages of preparing the environment for first time use.
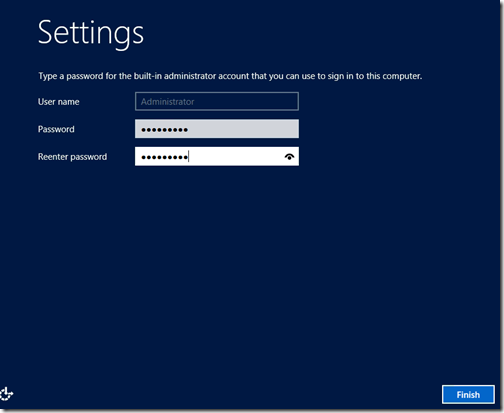
You will eventually be prompted to enter a password for the built-in Administrator account.
Click Finish
You will now be presented with the new Windows Login Screen, which is a fair change to what we have been accustomed to with previous releases of Windows Server.
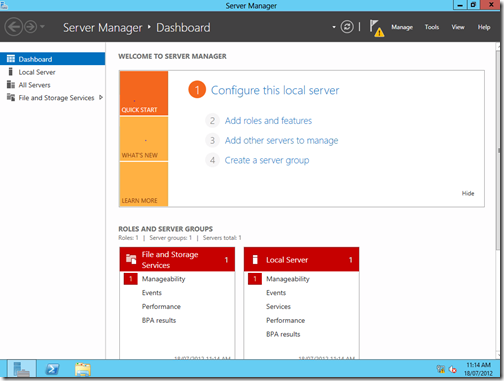
You will be presented with the new Server Manager Screen which really simplifies the administration and configuration of your new server. Our main goal for this article is to configure Active Directory and its related services such as DNS.
To do so, from the Server Manager > Dashboard screen, click on Local Server and then click on the computer name hyperlink.
Click Change, enter a more desirable Computer Name and then click OK.
You will then be prompted to restart your computer to apply the changes. Click Ok and then Click on restart now.
After your computer has restarted, we will be presented with the Server Manager Screen. Now we are ready to configure this server as an Active Directory Controller.
Adding the Active Directory Domain Services Role
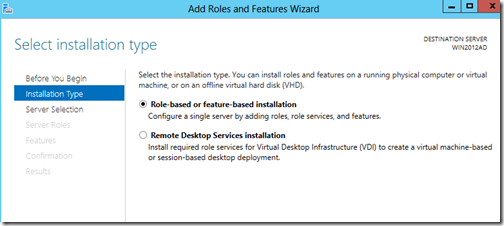
From the Dashboard click on “Add roles and features”. You will be presented with the “Before you begin screen. Click Next. In the “Installation Type” screen click on “Role-base or feature-based installation”.
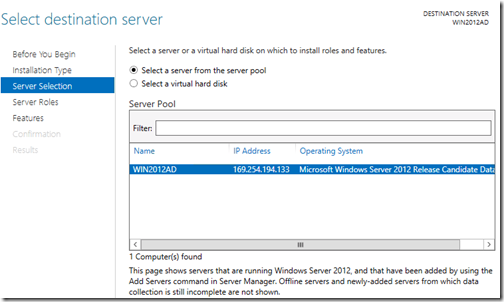
You will be presented with the following screen asking you to select a destination server. This is a new feature of Windows 2012 where you have the ability to deploy roles and features to remote servers and even offline virtual hard disks.
In our case, we are selecting the current server from the server pool.
We are now back in familiar territory (if you have worked with Windows 2008 Server) and we will select the “Active Directory Domain Services” and DNS Server if it hasn’t already been provisioned.
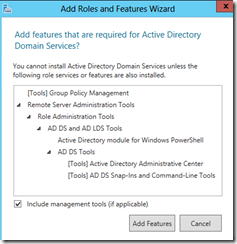
You will then be prompted to add features that are required for Active Directory Domain Services.Click on Add Features
Click Next
If you want to add additional features, you can do so from the next screen, otherwise click Next
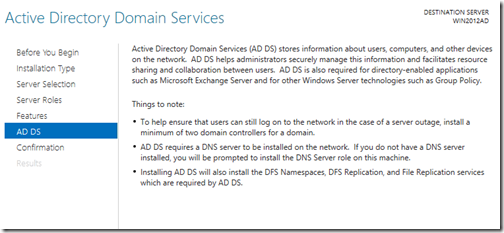
You will now be presented with the Active Directory Domain Services (AD DS) screen outlining some information about AD DS and its requirements. You will notice that DNS is a MUST and has always been the case.Click next
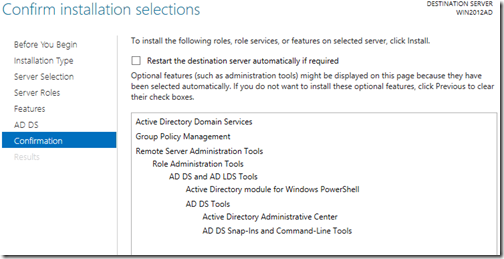
You now provided with a summary of installation selections
The installation will now beginUpon completion you will be presented with an installation succeeded message.
Click Close.
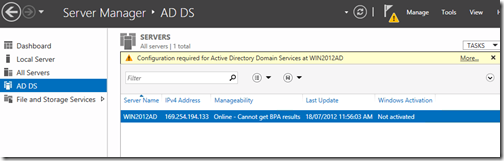
Back in Server Manager, you will notice that AD DS has been added to the left navigation tree. Click on it and then click on More on the right navigation pane where it states that Configuration is required for Active Directory Domain Services.
You will now be presented with the All Servers Task Details, in which you will click on Promote this server to a domain controller under Action.
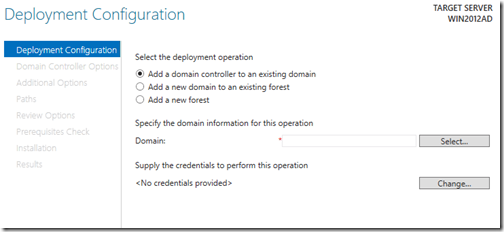
The Deployment Configuration screen appears and we will select “Add a new forest” as this is the first domain controller.
Enter your Root domain name and then click Next.
The following screen will then appear in which you will enter and select your Domain Controller Options.
You will then get the below warning in which you can ignore for now.Click Next
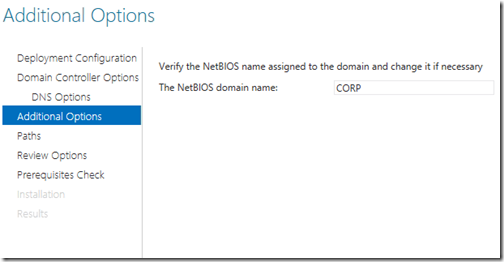
The NetBIOS domain name will then be inputted automatically. In the event of a conflict, it will suggest an alternative by appending the original name with a 0.
Click Next
Confirm or change the locations of your database folder, log folder and SYSVOL folder.
Click Next
Review your selections and then Click Next.
If all of the prerequisites checks have passed successfully, you will be able to click on Install to proceed.Click Install
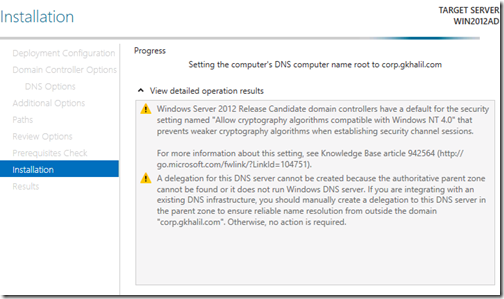
The installation will now proceed and you will see the progress being displayed.
The computer will most likely restart on its own to complete the installation so don’t be alarmed if it does. You will receive a brief warning advising so.
Upon restart, you should be able to login using your domain credentials for the user administrator.
So let’s add our first user! We can do so via the new Active Directory Administrative Center or via the well known Active Directory Users and Computers. For something different, lets try the former.
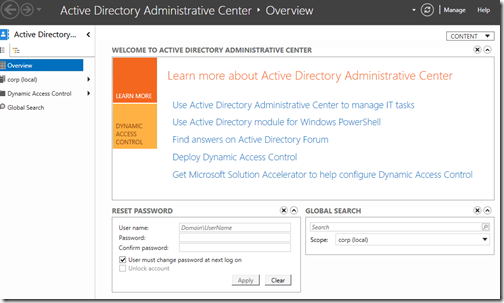
Once Server Manager has launched, click on Tools > Active Directory Administrative Center
You will be greeted with the below Welcome screen.
Click on your domain on the left navigation pane, in my instance it is corp (local).Let’s begin by creating our first Organizational Unit that will house our corporate users (I am not a fan of using the default Users). On the right navigation pane under Taks > <domain name> click on New and then select “Organizational Unit”.
Enter the mandatory details.
Click OK
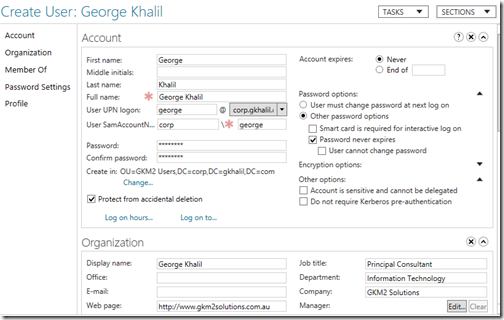
This will immediately create the Organizational Unit in the designated location. Double click on your newly created Organizational Unit and on the left navigation pane, select New User. The below screen appears in which you will fill in the necessary details.
Make sure you scroll down to the bottom and fill in all the necessary sections such as Groups, Profile Settings and Organization settings.
Once completed, Click OK.
Your newly created user will now be listed in the middle navigation pane.
As you can see it is relatively straight forward configuring your first domain controller in a new forest using Windows Server 2012, in particular if you have had experience with Windows Server 2008.